Vulnerability Scanning & 3rd-Party Modules Certification in N|Solid [8/10] The best APM for Node, layer by layer.
NCM —NodeSource Certified Modules— is the secure, reliable way to take advantage of the massive ecosystem of Node.js packages. Certified modules are compatible with Node LTS and monitored continuously to identify risk over time.
Certification guarantees no security vulnerabilities or unverified code in modules or dependencies and is easy to set up and manage. No workflow changes are required.
- Advantage: Know all of the potential vulnerabilities within your application.
- Benefit: Understand security risks and how to resolve them.
Why NCM it's an essential tool for a Node.js Developer?
Probably as a developer you have asked yourself these questions🕵️, if not, it is time to ask them out loud:
- Are you using the right npm packages?
- Are you using packages with known vulnerabilities?
- Do they have reasonable code quality?
- Do they include licenses that are compatible with your business?
Solving these questions and zooming in to the specific NCM is Security, Compliance, and curation tool around the 3rd-Party Node.js & JavaScript package ecosystem.
It is designed to be used in conjunction with npm to provide a layer of protection against known security vulnerabilities and potential license compliance issues and provide general quality or risk assessment information to improve your ability to work with the 3rd-party ecosystem.
 Img 1 - Introducing Nodesource Certified Modules - NCM
Img 1 - Introducing Nodesource Certified Modules - NCM
NCM provides actionable insights and presented risk levels; this helps to understand the level of risk and how to mitigate it. The Static analysis will provide:
- ✅ Security
- ✅ Compliance
- ✅ Code quality (checking packages)
Other products on the market don't do all three checks; another differentiator is the offline mode; you can scan your security vulnerabilities without being live. This helps you understand the level of risk exposure and how to mitigate it.
How does NCM in N|Solid work?
NCM provides you and your teams with actionable insights into the risk levels present in your use of third-party packages; using a series of tests; we score packages on npm to look for a number of weighted criteria.
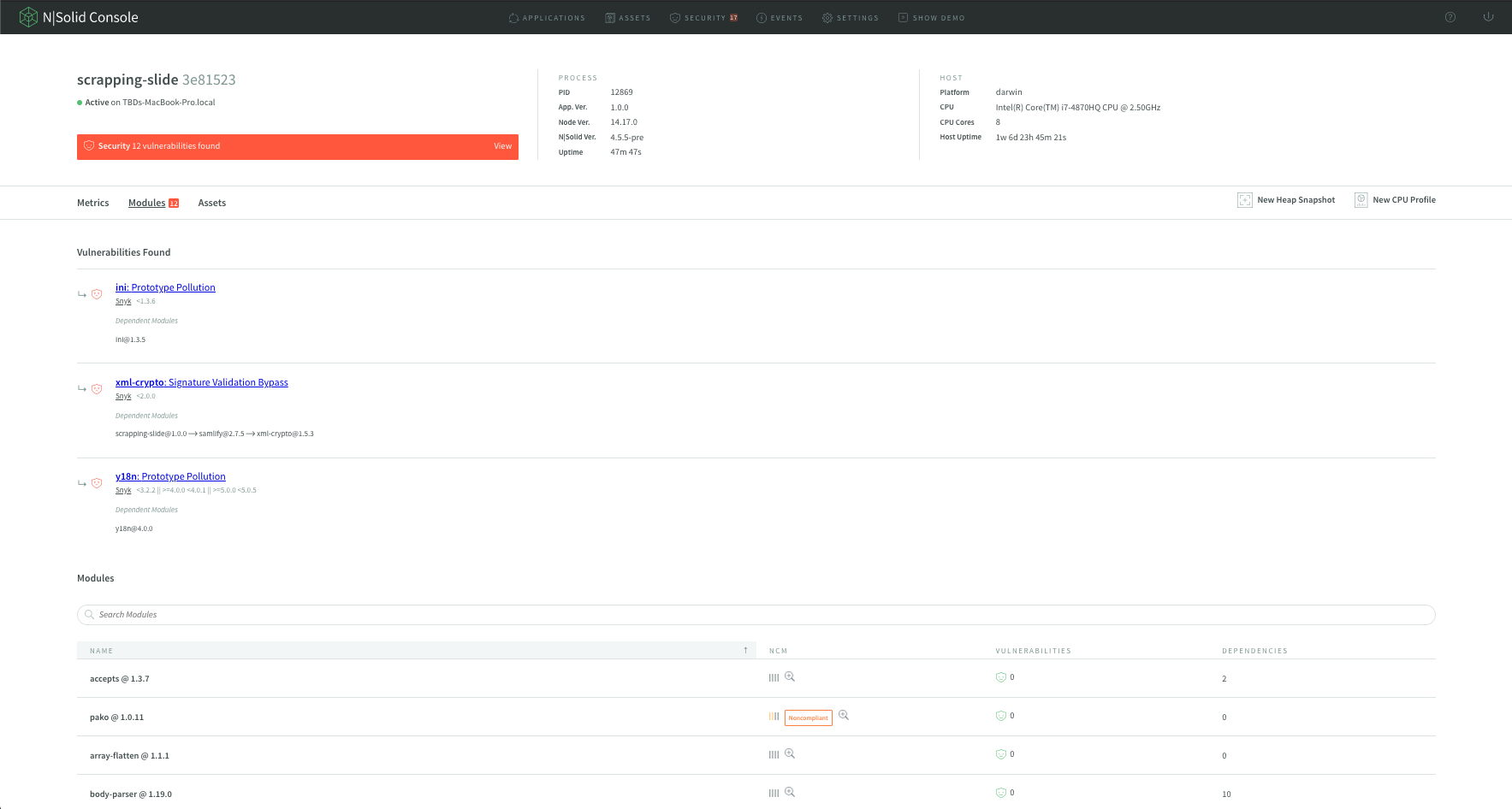 Img 2 - NodeSource Certified Modules - NCM in N|Solid
Img 2 - NodeSource Certified Modules - NCM in N|Solid
NCM provides a 0-100 trust score and assesses packages based on Security, compliance, package risk, and quality attributes. Security vulnerabilities have severity levels. Each severity level contributed to the respective risk level:
 Img 3 - NCM Score Details
Img 3 - NCM Score Details
__NOTE: __ If your application requires an uncertified package and there are no certified alternatives, uncertified packages can be whitelisted in your registry, allowing installation.
Img 4 - NCM Managing Registry
The NCM command line tool allows for whitelisting uncertified packages and more. Management of your registry, including:
- whitelist management
- score reporting
- visualization of package tree with scores
What does "Certified" mean?
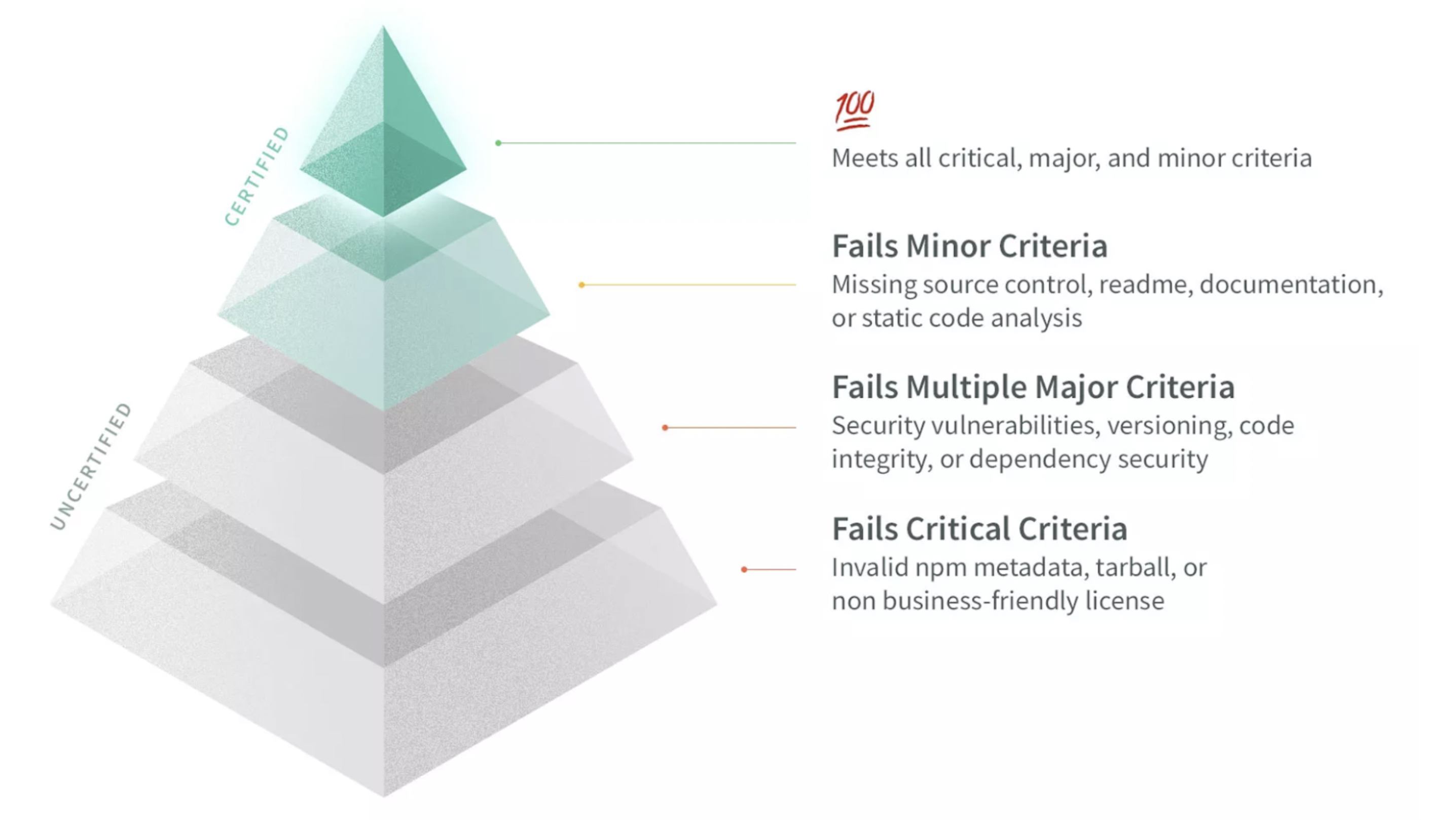 Img 5 - NCM NodeSource Certified Modules
Img 5 - NCM NodeSource Certified Modules
NodeSource evaluates publicly available packages based on weighted criteria to determine a "trust score" for each package, monitoring for security vulnerabilities on an ongoing basis to identify emerging risks. With Certified Modules, NodeSource provides a level of trust in each of the modules used.
With NCM, you have these capabilities:
- Know that the Node.js packages powering your Businesses are high quality and safe to use.
- All of the packages on the npm registry have been scored, allowing you to search for the certified packages that are right for your application.
- When packages don't meet our certification criteria, see the details for where it falls short.
- When using your Certified Modules registry, only certified packages will be installable. When attempting to install an uncertified module, the npm client will report an error indicating that the requested package is not certified and will not be installed.
 Img 6 - Confidence - NodeSource Certified Modules NCM
Img 6 - Confidence - NodeSource Certified Modules NCM
NCM provinces full customization in:
- Service Tokens (you can define policies inside accounts in N|Solid).
- CI Processes
This prevents all customers from deploying vulnerable applications; this checks the Security before going live, then NCM checks our database for vulnerabilities.
We rely on validated providers:
 Img 7 - Data Providers - NodeSource Certified Modules NCM
Img 7 - Data Providers - NodeSource Certified Modules NCM
Stops any application with NCM in Strict mode
The N|Solid strict mode allows custom configuration using JSON-based configuration. The N|Solid strict mode can be used with the prompt nsolid-strict instead of the well-known nsolid; the key difference between strict and regular mode is that the strict mode will stop any application with encountered vulnerabilities identified by the NCM.
Run the prompt nsolid-strict with an option --config or -c to edit the JSON-based configuration file using your system's default text editor.
If you want to know more about how NCM Prevents npm Substitution Attacks or our integration directly with Github, we invite you to read 'Avoiding npm substitution attacks using NCM'.
Try NCM - NodeSource Certified Modules Now!
Run:
$ npm install -g ncm-cli
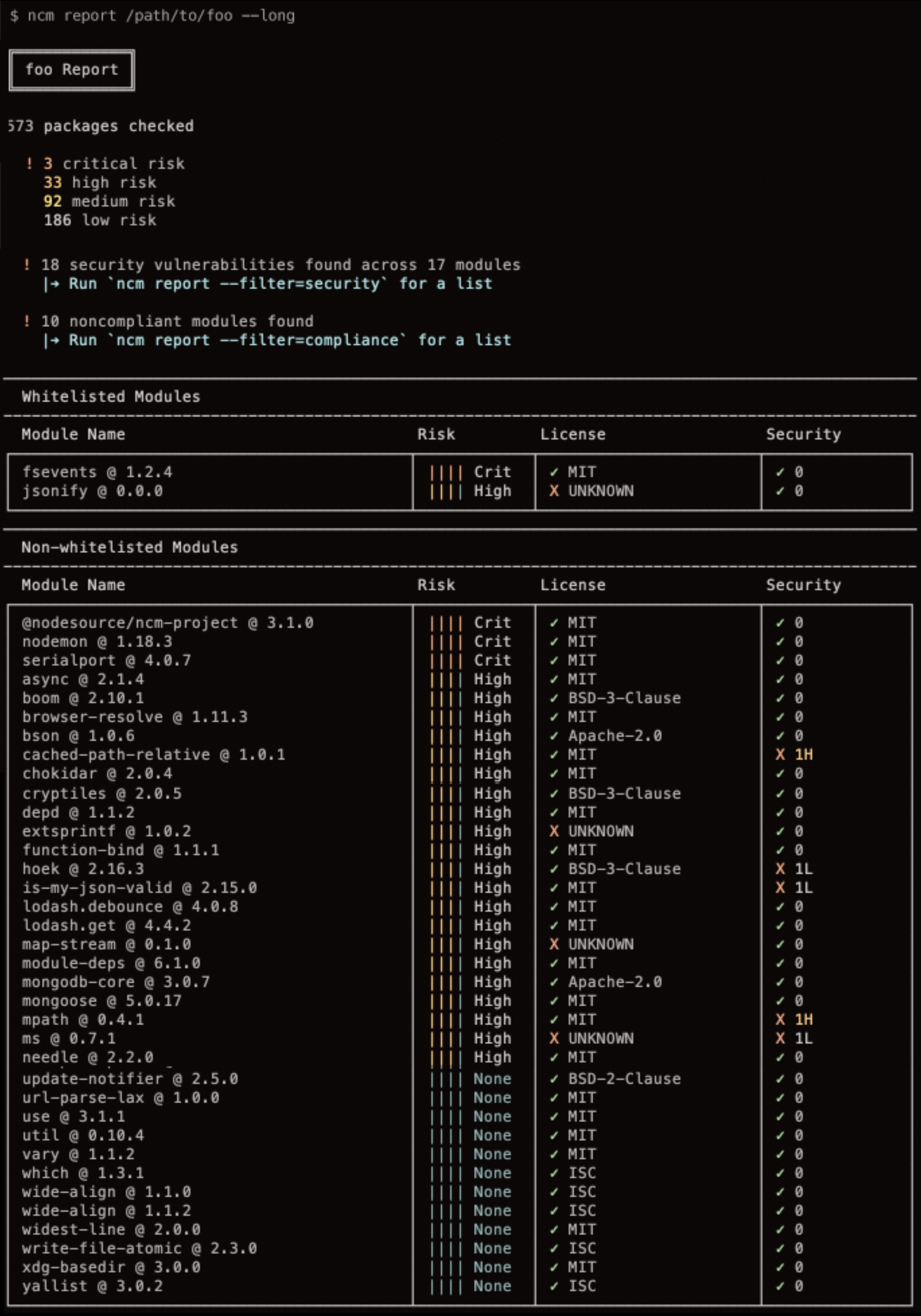
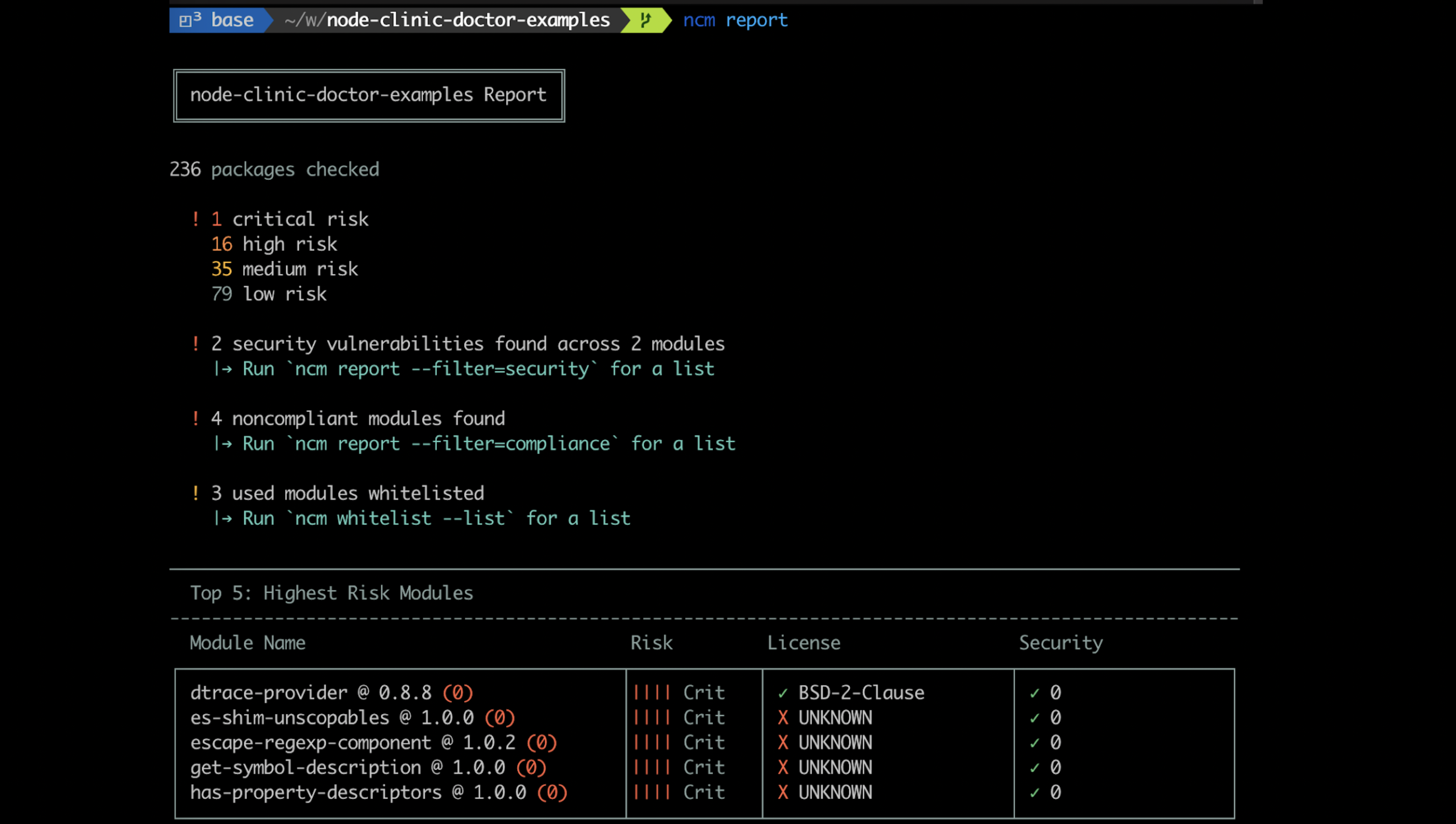
Generates a project-wide report of directory risk and quality of installed or specified packages. The top five riskiest modules detected will be displayed alongside a concise project report.
 Img 8 - Report - NodeSource Certified Modules NCM
Img 8 - Report - NodeSource Certified Modules NCM
The directory to generate a report from may be specified via ncm report <dir>. Defaults to using the current working directory.
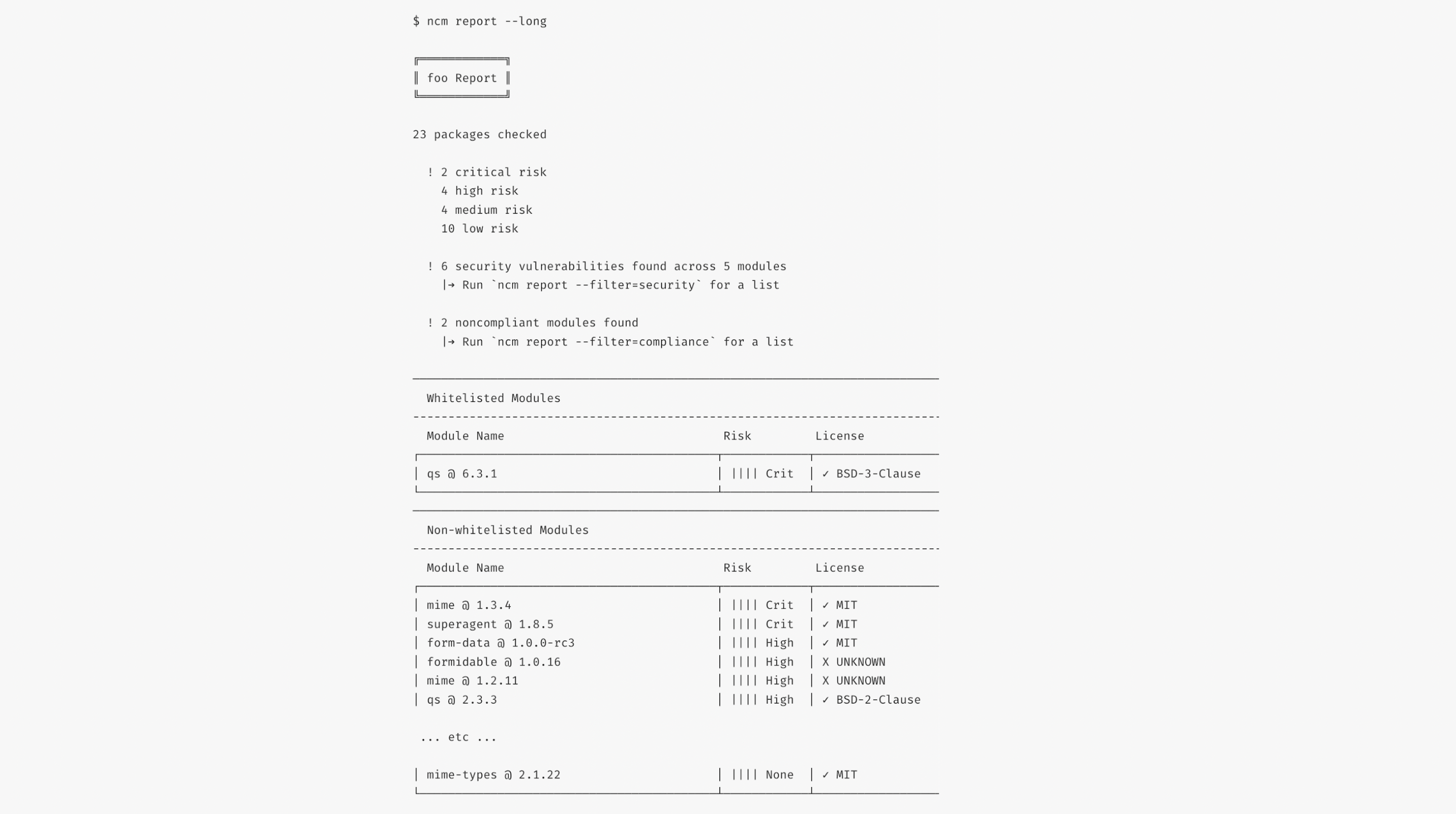 Img 9 - Full Report - NodeSource Certified Modules NCM
Img 9 - Full Report - NodeSource Certified Modules NCM
A report with a list of all modules can be generated by passing --long , -l.
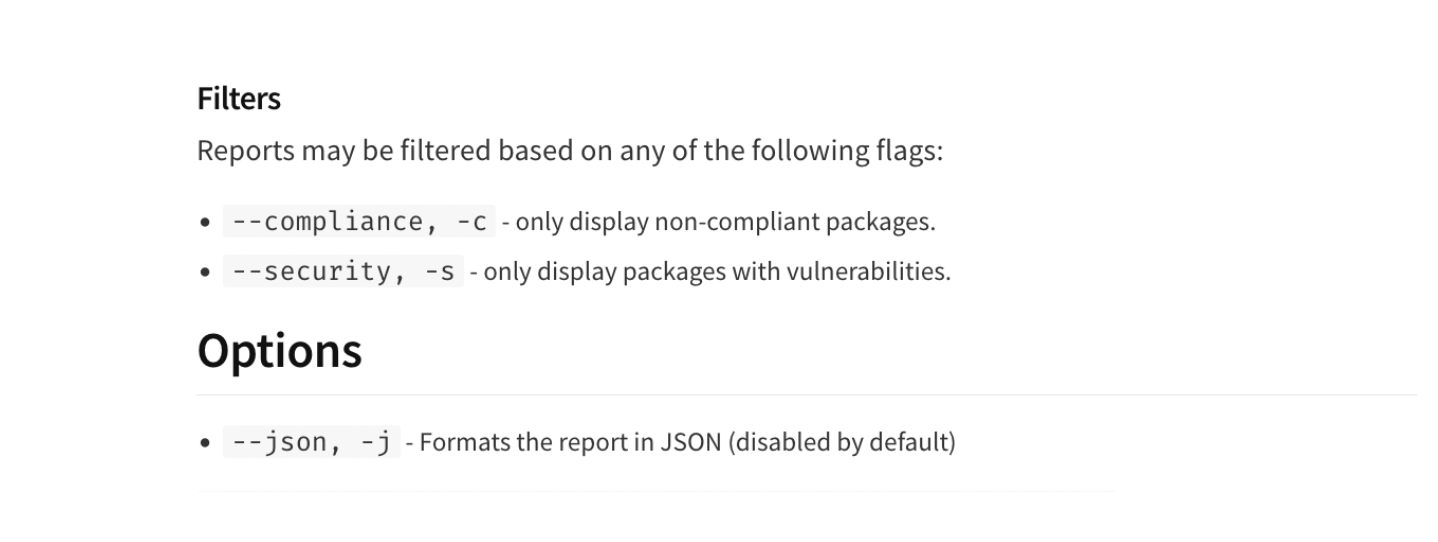 Img 10 - Filters - NodeSource Certified Modules NCM
Img 10 - Filters - NodeSource Certified Modules NCM
ncm details <module{@version}>
Returns a detailed report about a specific module version. Defaults to using the latest version as published to npm if no version is provided.
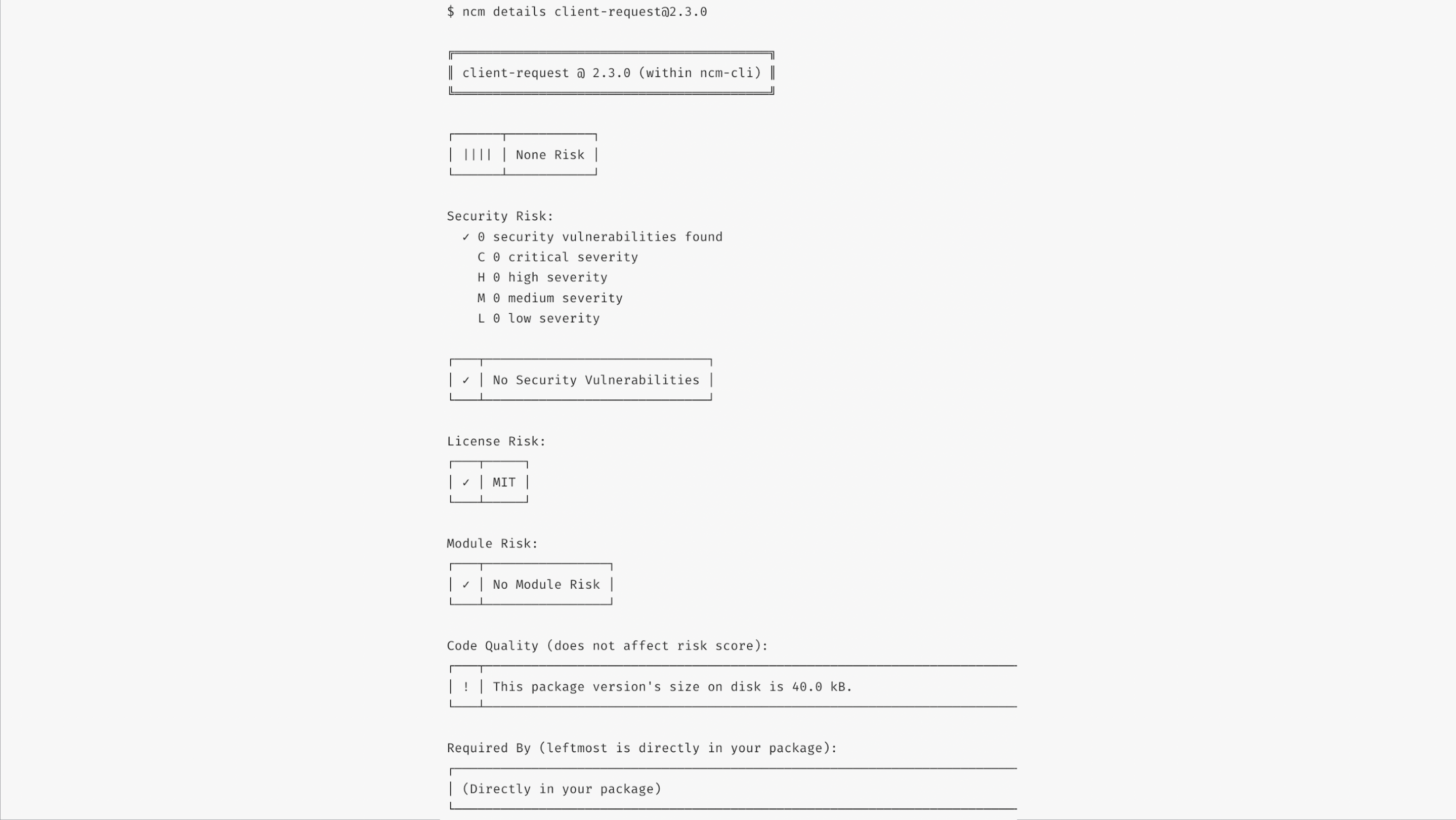 Img 11 - Details - NodeSource Certified Modules NCM
Img 11 - Details - NodeSource Certified Modules NCM
ncm install <module{@version}>
Runs and displays ncm details <module{@version}> with an interactive confirmation prompt.
If confirmed, attempts to run npm install <module{@version}> with any additional options provided.
The config keys installBin and installCmd can adjust this to work with other package installers if necessary. For more information, see ncm config --help.
NCM whitelist
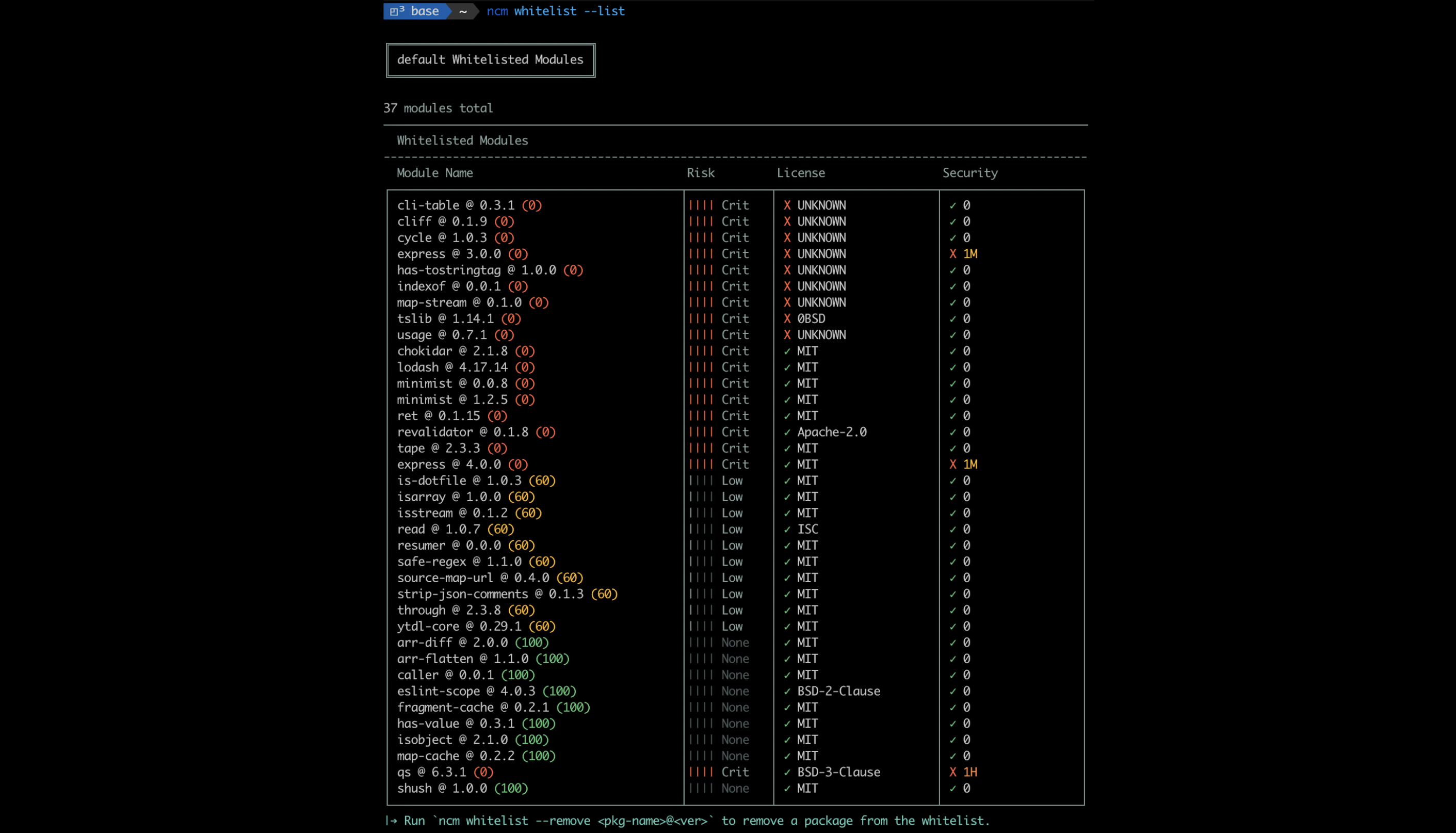 Img 12 - Whitelisting Packages - NodeSource Certified Modules NCM
Img 12 - Whitelisting Packages - NodeSource Certified Modules NCM
Display or modify your NodeSource organization’s module whitelist.
ncm whitelist --list:
- Returns a list containing each module in your NodeSource organization’s whitelist.
- Public modules are listed alongside their risk score, license compliance, and security summary.
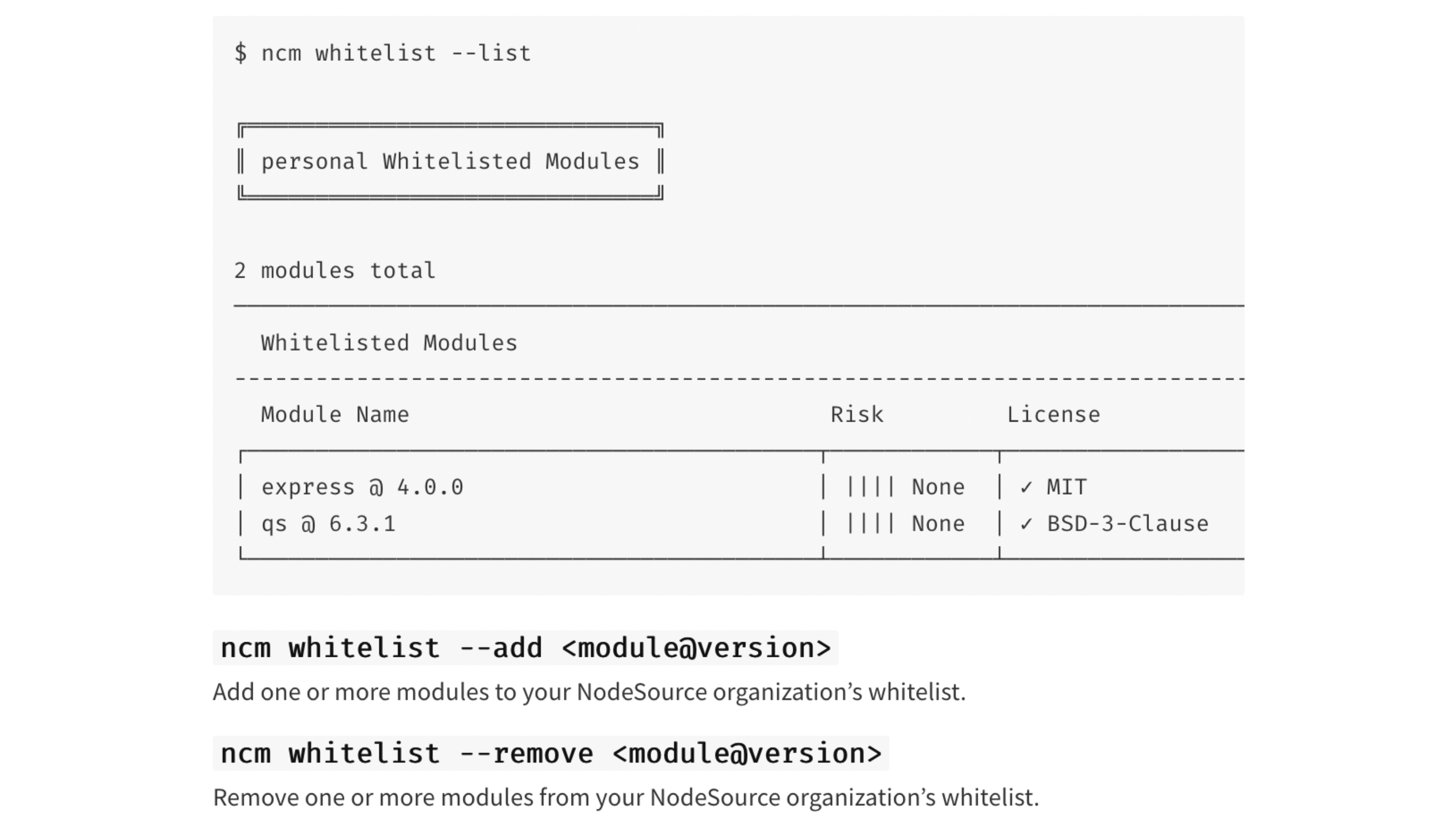 Img 13 - Whitelisting - NodeSource Certified Modules NCM
Img 13 - Whitelisting - NodeSource Certified Modules NCM
ncm orgs
Change your active NodeSource organization, which impacts the whitelist. Defaults to an interactive prompt. By passing an <orgname>, the interactive part may be skipped. ***Input is case sensitive.
ncm config
Access to various configuration settings. For more information, use the help command: ncm config --help
Avoiding npm substitution attacks using NCM
Run ncm install instead of npm install to avoid npm substitution attacks, which automatically prevent public versions from replacing or merging with private packages.
NCM verifies all of the packages defined in package.json to scan except scoped packages because the scoped packages are fundamentally not vulnerable to npm substitution attacks.
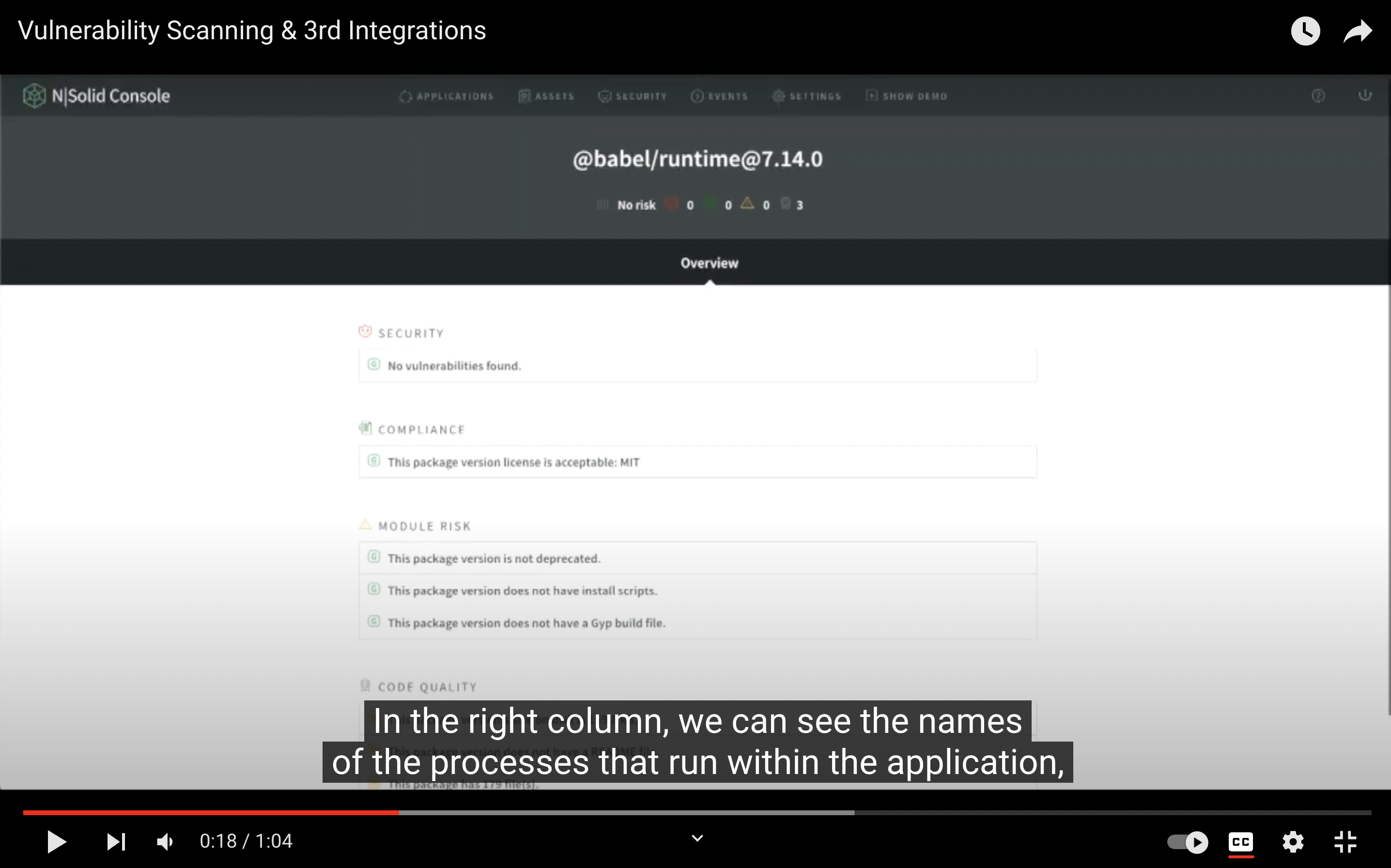
Demo Video — NCM in N|Solid
__NOTE: __ For a better experience, you can activate the closed captions in the video. They are available in English.
The N|Solid Console can be configured to perform periodic verification of all packages loaded by all N|Solid processes.
- All loaded packages are verified against a list of known vulnerabilities.
- Information about each vulnerability will be reported in the Console when new vulnerabilities are found. Notification options can be configured.
- Provides actionable insights into the risk levels in your use of third-party packages.
Want to try N|Solid?
Do it right now! 🏃🏿♂️🏃♀️, We release in Openjs World 2022 some codes to redeem 50% in 8 or 12 processes in our SaaS version.
50% OFF USING:
- 8 processes OPENJS-8T
- 12 processes OPENJS-12T
Or sign up for our FREE option for 4 processes and get started with N|Solid!
To check out the top 10 features and more in N|Solid, sign up to create your account or sign in at the top right corner of our main page. More information is available here.