Avoiding npm substitution attacks using NCM
NodeSource is excited to announce its latest NodeSource Certified Modules - NCM - release. NCM, provides developers and software teams with actionable insights into the risk levels that are present in your use of third-party packages. This release includes updates to avoid npm substitution attacks and also a GitHub Integration: Code risk, compliance and security action for PRs on Node.js.
It is recommended to upgrade ASAP and if you are not yet using N|Solid, the best way to monitor and secure your Node.js, try it for free here.
Last month a crafty hacker identified a major security risk for companies that download npm packages for Node.js. This attack could have significant risks for every organization. Our Node.js experts investigated the issue to help our customers avoid the issue altogether. For more information about this attack, read the hackers own account of the story blog.
The result of our work is this new capability being released today into N|Solid. We are extremely proud of the work, it's a very elegant solution to an important issue.
How Does It Work?
Run ncm install instead of npm install to avoid npm substitution attacks, which automatically prevents public versions from replacing or merging with private packages.
How NCM Prevents npm Substitution Attacks?
First of all, NCM gets all of the packages defined in package.json to scan except scoped packages because the scoped packages are fundamentally not vulnerable to npm substitution attacks.
To understand how NCM verifies whether a package is vulnerable to npm substitution attacks, let’s look at the JSON structure of npm registry below:
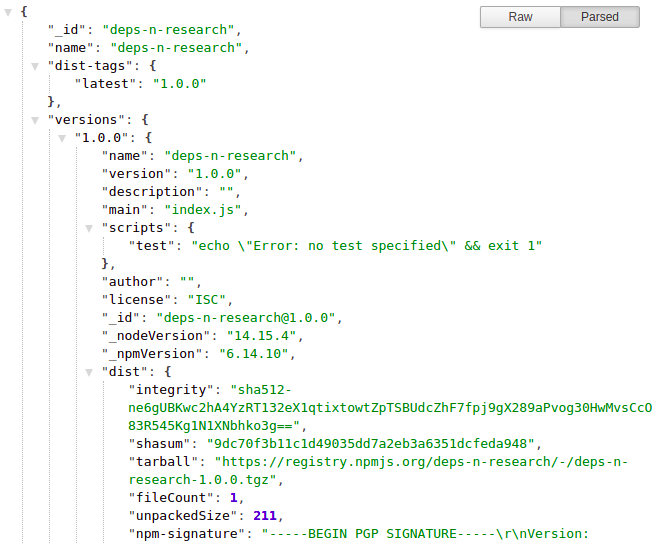
Every npm package has the key versions. By comparing the nested key versions.dist.integrity which is a unique value used for checking the integrity of the package, NCM considers a package is vulnerable to dependency substitution attacks by the two conditions below:
- There’s a package that has been published to both public registry and internal registry using the same package name
- The value of
versions.dist.integrityof the package in the internal registry does not match that in the public registry
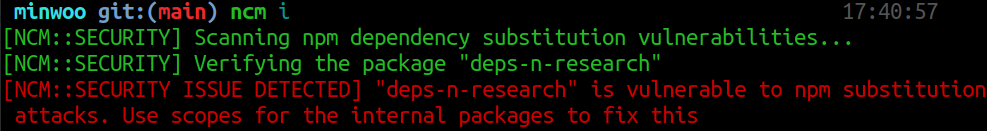
if there’s any package that meets the conditions above, NCM will output an error message to show them suggesting users use scopes for the internal packages and exit with status code 1 as below:
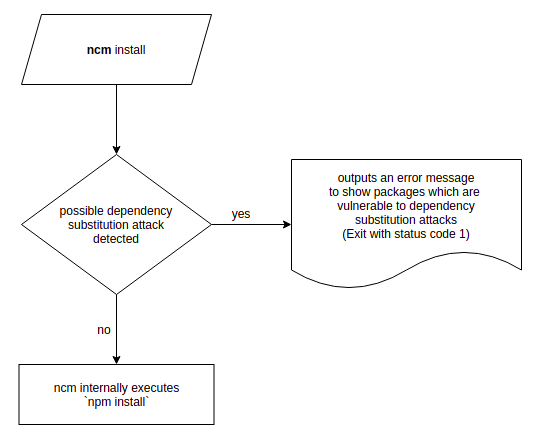
Note: The flowchart of ncm install:
Improvements / Optimization
- Leverage a cache for public packages which doesn’t need verification
- Tweak verification tasks run concurrently
GitHub Integration: Code risk, compliance and security action for PRs on Node.js
This integration enables a lightweight CI workflow that runs specific checks on your organization’s PRs.
This is a new way to consume NCM, with better security management, code risk and code quality assessment, laterally integrated with your CICD flow and lightweight CLI for all your systems.
For this, we develop a GitHub action that enables NCM2 checks for your organization’s PR by integrating it into a workflow that passess all failed PRs checks based on a package risks score and provides annotations with details for each package assessment.
For more details about this integration, check out this video.
Need a helping hand?
If you have any questions, please feel free to contact us at info@nodesource.com.
To get the best out of Node.js, start a free trial of N|Solid, an augmented version of the Node.js runtime, enhanced to deliver low-impact performance insights and greater security for mission-critical Node.js applications. #KnowYourNode