Announcing Module Risk and Security for AWS Lambda
Securing serverless applications can be a challenge. We are excited to launch the first-ever Module Risk and Security feature for third-party public packages in AWS Lambda. NodeSource now provides you with clear indicators of known security issues as well as the overall risk level of packages used by AWS Lambda functions running on Node.js.
Our newest feature in N|Solid for AWS Lambda provides users with an up-to-date risk, compliance and security assessment report for installed packages and dependencies, with clear indicators of the overall risk level in your application. In addition to low-impact performance monitoring for Lambda functions, NodeSource now makes it easier to better understand the security and risk for third-party public packages used in your serverless applications.
This new feature is based on the NCM 2 Certification pipeline which also powers the NCM 2 CLI.
How does this work?
The Modules feature in N|Solid for AWS Lambda is powered by the NCM 2 Certification Pipeline. It provides actionable insights about the risk levels that are present in third-party packages used in your Lambda functions. Using a series of tests, NodeSource checks packages from the npm registry and computes a score based on a number of weighted criteria.
N|Solid for AWS Lambda continuously scans your projects for existing security vulnerabilities, license concerns, code risk and code quality.
Existing N|Solid for AWS Lambda users will see a brand-new Modules tab in your application dashboard. Navigating to this tab will show you an up-to-date risk, compliance, quality and security assessment report.
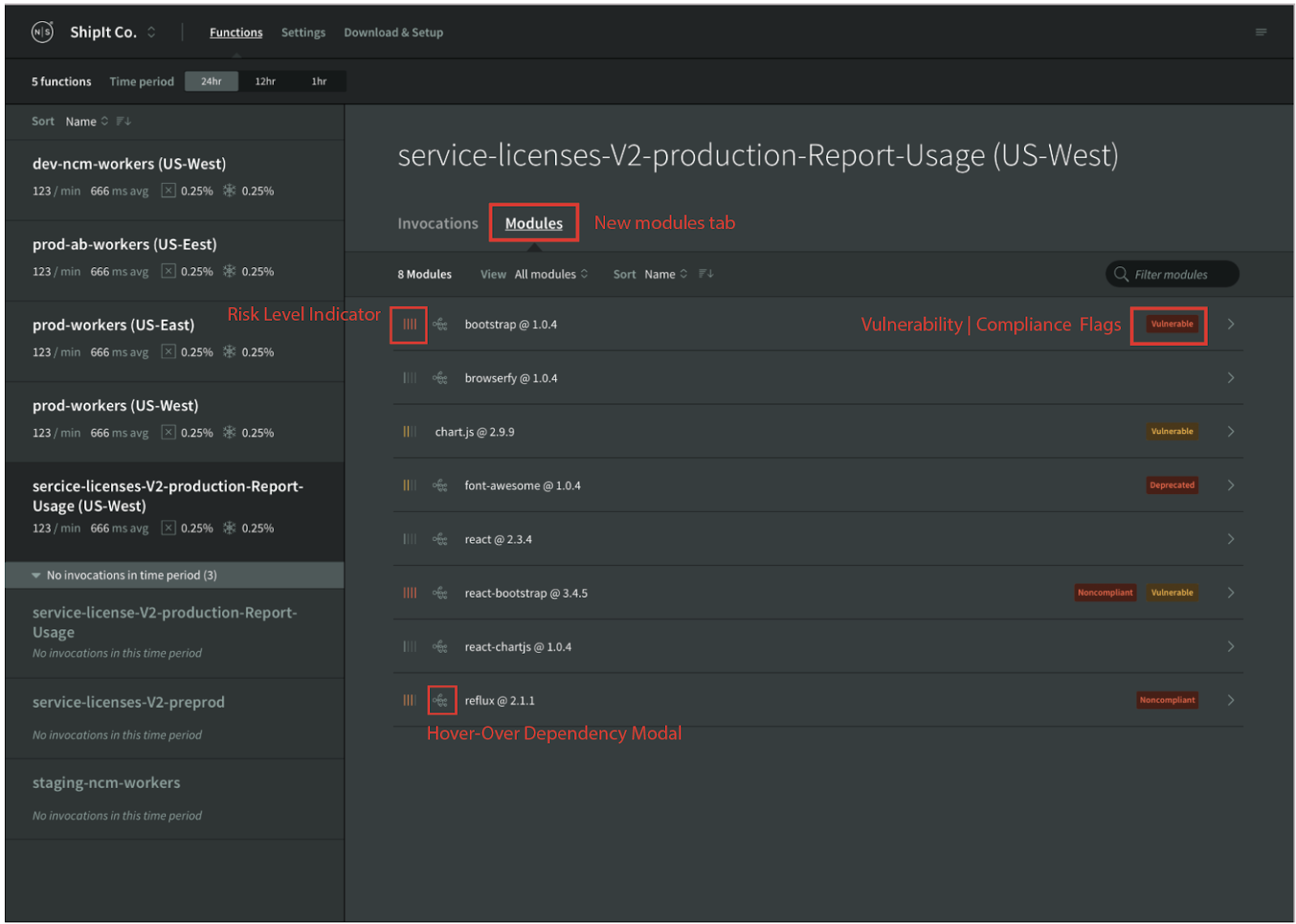
Module List View
The Module List View delivers a higher-level overview of:
- Modules used in the application
- Warning flags for security vulnerability, compliance concern, or deprecated modules
- A code risk indicator indicating the known risk level (low, medium, high, or critical) for each installed module
If a module was added to your function as a dependency of another module, hovering over the module name in the Module List View will show a tooltip indicating which modules required the dependency.
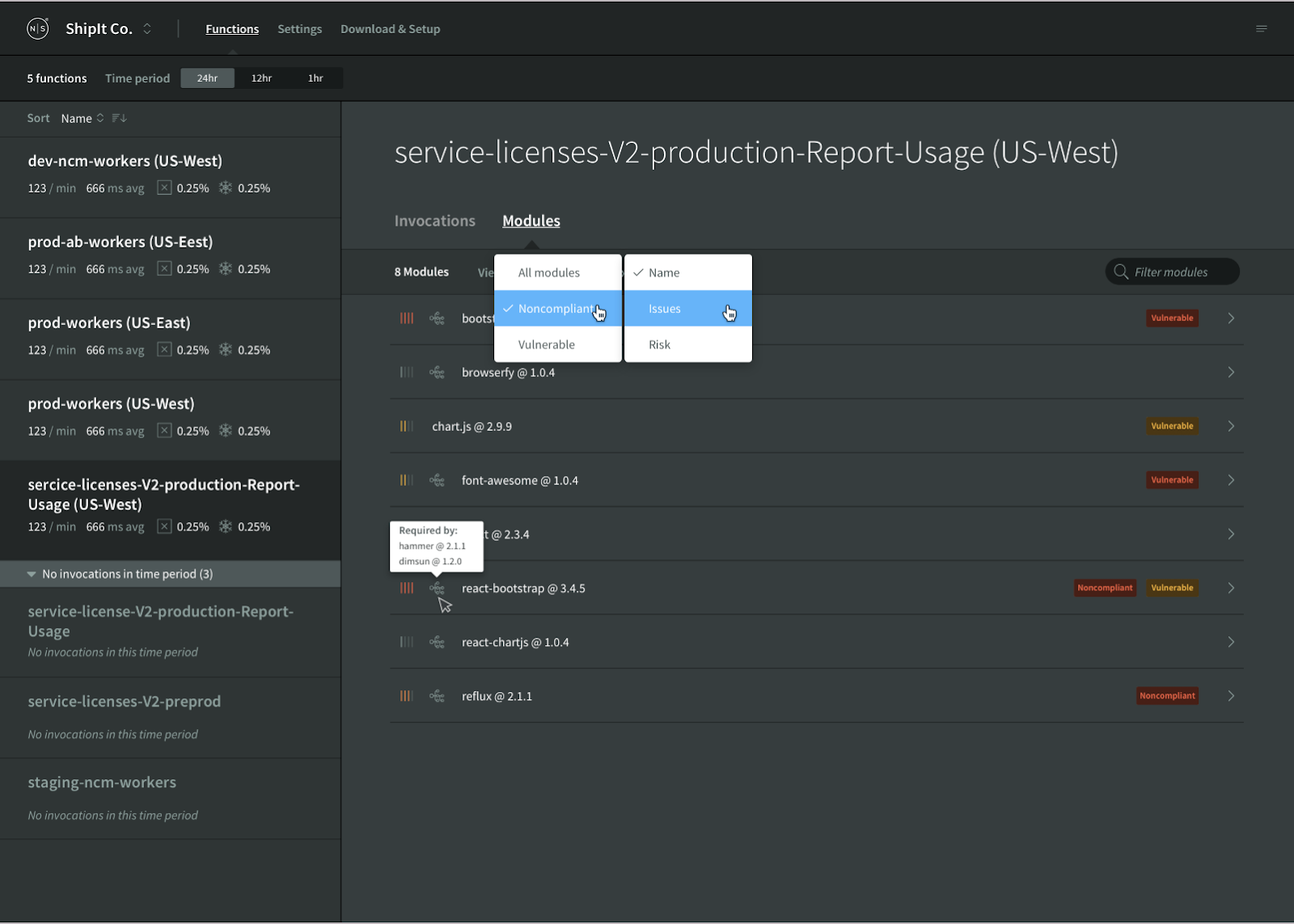
Module Details View
From the Module List View, you can click to view more details of an individual package, presented in the Module Details View:
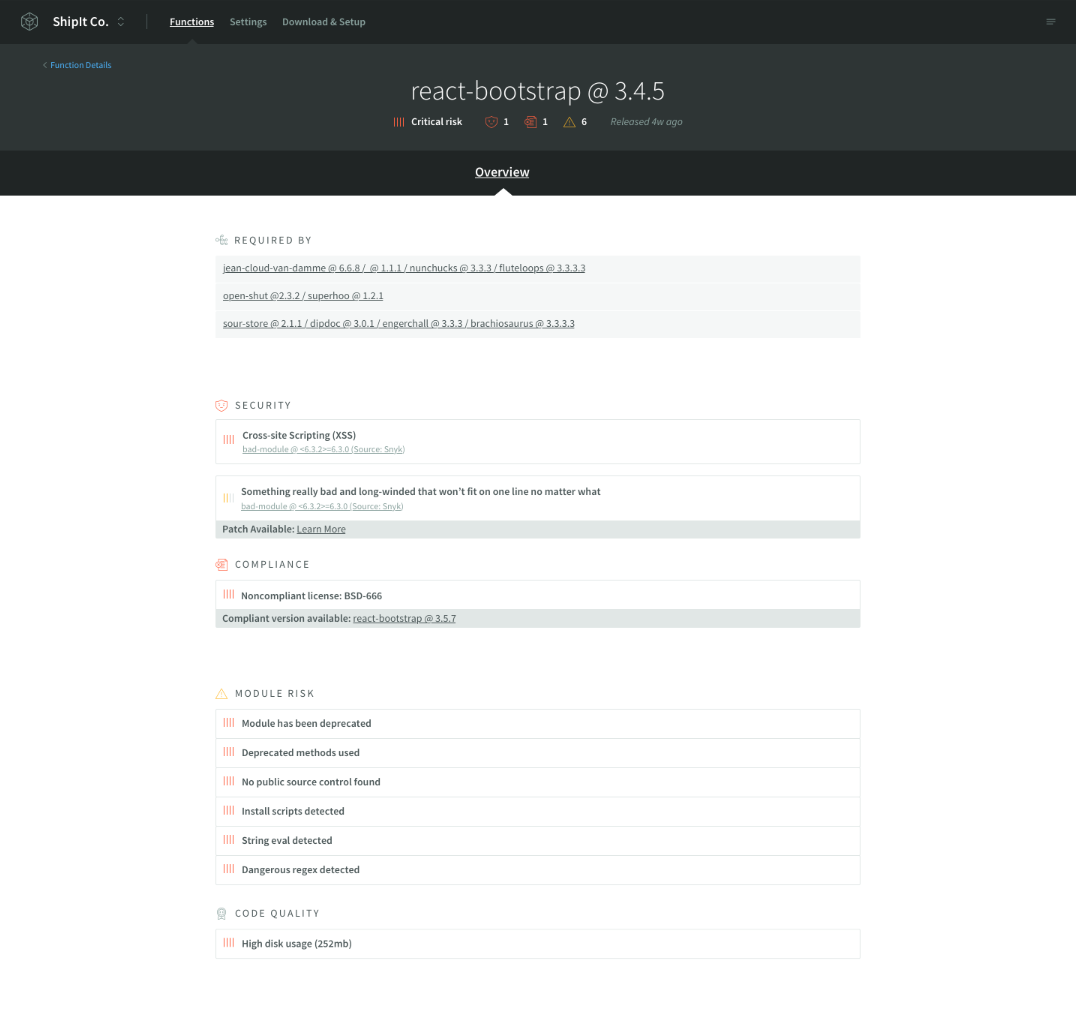
This view provides a detailed account of each third-party module in your serverless function:
- Module Name and Report Summary: A high level overview that delivers a quick summary of the module's:
- Risk Score
- Number and severity of security vulnerabilities
- Number of compliance concerns
- Number of Risk Factors identified
- Required By: A detailed list of dependency-paths that indicate which modules in your function’s dependency require said module
- Security Vulnerability Report: A list of known security vulnerabilities, their severity and link to the Snyk report
- Compliance Report: A list of known compliance concerns which NodeSource believes has elevated legal and/or security implications. The license score is intended to indicate that a given module has a license which is permissible for use, allows redistribution and modification, and does not require source disclosure.
- Module Risk: The Risk group is for criteria which are intended to indicate whether a package's usage or installation may be abnormally risky
- Code Quality: The Quality group is for criteria which are intended to indicate whether a package is consistent with good open-source practices.