RBAC - Role Based Access Control
Last week, we announced NSolid 3.11.1, which introduces Role Based Access Control along with support for Node.js Erbium v12.16.2 and Dubnium v10.20.1. You can read here for more information.
NodeSource’s Role Based Access Control feature empowers Org Admins to create, define, manage and assign roles that provide access privileges to distinct user-actions and/or views in the NSolid Console and accounts.nodesource.com. All role definitions and role assignments are managed via NSolid’s Central Access Control Nexus accounts.nodesource.com, which also supports SAML-based federated authentication via OneLogin, PingID and Okta.
The system comes with a set of pre-made roles but permits full customization of permissions per role as well as the creation and deletion of existing roles.
How it works:
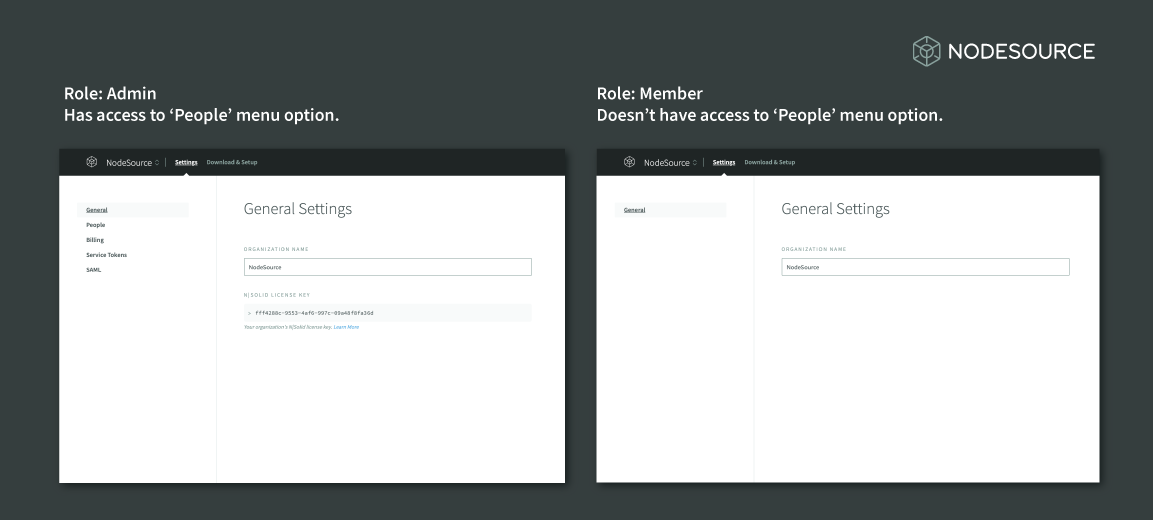
The following shows the NodeSource’s central control-nexus, accounts.nodesource.com, from the perspective of two different users:
- The ‘Admin’ has access to the Organization’s ‘People’s’ Tab where they can invite team-members, define and assign RBAC roles.
- The ‘Member’ doesn’t have access to the ‘People’s’ Tab. To them the tab isn’t visible.
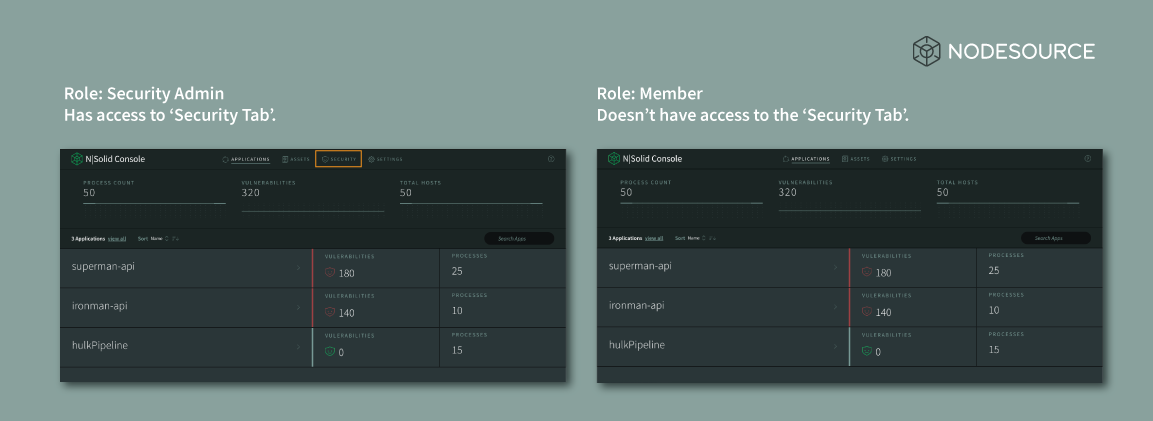
Similarly, in the NSolid Console a ‘Security Admin’ will be granted access to the Console’s Security Tab, while a user with the ‘Member’ role won’t be allowed to access this option:
You can see a list of permissions that can be aggregated into new roles and/or added to existing roles here.
RBAC - Pre-Configured Roles
Pre-configured configured roles include:
The Admin role has access to all permissions for both NodeSource'c Central Management Platform accounts.nodesource.com and the NSolid Console. This includes accessing billing, license keys, as well as managing RBAC permissions and, team members, and SAML integrations in accounts. This role also features full permissions for all features available in the NSolid Console.
The pre-configured Ops Admins serves to meet the needs of DevOps Managers acting at the deployment level. They have full access to the NSolid Console, but are unable to hide security vulnerabilities unless an Admin role modifies this permission. This can be accomplished through the org’s setting page in accounts.nodesource.com which features limited access for this role.
The pre-configured The Security Admin role is a security-focused that acts at the application level. , This role retains access to NodeSource's Central Account Management Platform accounts.nodesource.com, but users with this role are unable to access most of the settings reserved for managing an organization’s NSolid deployment via the Admin role. In the NSolid Console Security Admins can monitor applications, view and hide security vulnerabilities, as well as manage most diagnostic actions.
The pre-configured Member role, is focused on monitoring and diagnostics of application performance only. As with all roles, this role can be modified via NodeSource’s Central Account Management Platform. Members have access to accounts.nodesource.com but are unable to view a number of Settings reserved to Admins.
<table style=“width:100%“> Admin Security Admin Ops Admin Member
